
Overview
Like banknotes, ecash can be withdrawn from and deposited to transaction demand deposit accounts. And like banknotes, one person can transfer possession of a given amount of ecash™ to another person. But unlike cash, when a customer pays another customer an electronic bank will play an unobtrusive but essential role.To show how it all works we'll explain how a withdrawal works, then follow the ecash in a payment to a merchant. Combining these two transactions, we can then understand why the customer perceives that ecash is paid from person to person without involving any bank. Finally the withdrawal is explained in greater detail to illustrate the 'blind signature' concept, which is the foundation of the privacy feature, and explain why the bank cannot trace it's own money!
Simple Withdrawal of ecash
Figure 1 shows the two participants in the withdrawal transaction: the bank and customer, Alice. The digital coins that have been withdrawn from Alice's account at the bank are on their way to her PC. When they arrive, they will be stored along with some coins she already has on her hard disk.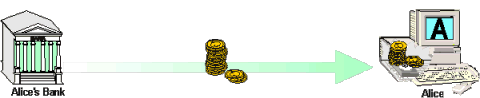
Figure 1 - Alice withdraws ecash from her bank account
No physical coins are involved in the actual system of course, but the messages include strings of digits, and each string corresponds to a different digital coin. Each coin has a denomination, or value, so that a purse of digital coins is managed automatically by Alice's ecash software. It decides which denominations to withdraw and which to spend in particular payments. (The ecash software keeps plenty of 'small change', but will prompt the user to contact the bank in the rare event that more change is needed before the next payment, to restructure its purse of coin denominations.)
An ecash Purchase
Now that Alice has some ecash on her hard drive, she can buy things from Bob's shop (as shown below).Having received a payment request from Bob, she agrees by ticking the 'Yes' box. Her ecash software chooses coins with the desired total value from the purse on her hard disk. Then it removes these coins and sends them over the network to Bob's shop. When it receives the coins, Bob's software automatically sends them on to the bank and waits for acceptance before sending the goods to Alice along with a receipt.

Figure 2 - Alice buys something from Bob
To ensure that each coin is used only once, the bank records the serial number of each coin in its spent coin database. If the coin serial number is already recorded, the bank has detected someone trying to spend the coin more than once and informs Bob that it is a worthless copy. If, as will be the usual case, no such serial number has been recorded, the bank stores it at that position and informs Bob that the coin is valid and the deposit is accepted.
Person-to-Person Cash
When a consumer receives a payment, the process could be the same. But some people may prefer that when they receive money, it be made available on their hard disk immediately, ready for spending; just like when someone hands them a five dollar bill. This user preference can be realized as depicted in Figure 3.The only difference between this payment from Alice to another consumer, Cindy, and the one Alice paid to Bob's shop in Figure 2, is what happens after the bank accepts the cash. In Figure 3, Cindy has configured her software to request the bank to withdraw the ecash she has just deposited and send it back to her PC as soon as the coins are accepted. (Actually Cindy's bank will check with Alice's bank to make sure that the coins deposited are good.) Now when Alice sends Cindy five dollars, new coins are immediately available to spend from Cindy's PC.

Figure 3 - person-to-person payment
How Privacy Is Protected
In the simple withdrawal of Figure 1, the bank created unique blank digital coins, validated them with its special digital stamp, and supplied them to Alice. This would normally allow the bank (at least in principle) to recognize the particular coins when they are later accepted in a payment. And this would tell the bank exactly which payments were made by Alice.By using 'blind signatures, a feature unique to ecash, the bank can be prevented from recognizing the coins as having come from a particular account. The idea is shown in Figure 4. Instead of the bank creating a blank coin, Alice's computer creates the coin itself at random. Then it hides the coin in a special digital envelope and sends it off to the bank. The bank withdraws one dollar from Alice's account and makes its special 'worth-one-dollar' digital validation like an embossed stamp on the envelope before returning it to Alice's computer.
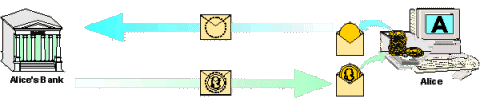
Figure 4 - Alice sends her coin for signature by the bank
Like an emboss, the blind signature mechanism lets the validating signature be applied through the envelope. When Alice's computer removes the envelope, it has obtained a coin of its own choice, validated by the bank's stamp. When she spends the coin, the bank must honor it and accept it as a valid payment because of the stamp. But because the bank is unable to recognize the coin, since it was hidden in the envelope when it was stamped, the bank cannot tell who made the payment. The bank which signed can verify that it made the signature, but it cannot link it back to a particular object or owner.
|
|
|